In the ever-evolving landscape of embedded systems, the convergence of functional safety and security has become paramount. As devices become more interconnected and integrated into critical infrastructure, ensuring their reliable operation and safeguarding against potential threats are non-negotiable aspects.
Functional Safety in Embedded Systems:
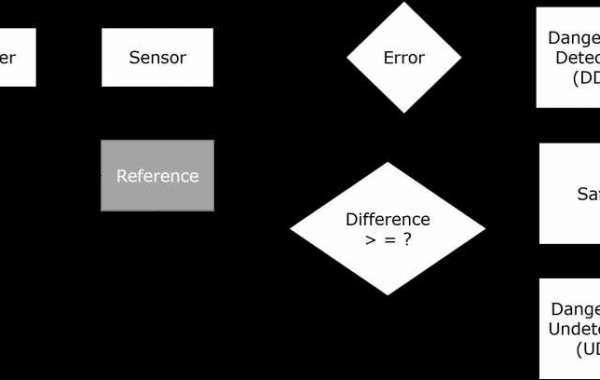
Functional safety in embedded systems revolves around the assurance that a device or system behaves predictably and safely, even in the presence of faults. In the context of embedded systems, this often involves mitigating risks associated with hardware and software failures. A robust functional safety strategy involves rigorous analysis, design considerations, and adherence to industry standards such as ISO 26262 for automotive systems or IEC 61508 for general embedded systems.
Security Challenges in Embedded Systems:
The escalating connectivity of embedded systems introduces a new dimension of challenges related to security. Threats such as unauthorized access, data breaches, and malicious attacks pose significant risks. Implementing security measures is imperative to protect sensitive data, ensure the integrity of the system, and maintain user trust.
UVM Register Model:
The Universal Verification Methodology (UVM) Register Model serves as a pivotal tool in addressing both functional safety and security concerns in embedded systems.
At its core, a UVM Register Model provides an abstract representation of the registers within a hardware design. These registers are vital components that control and monitor the behavior of the system. By encapsulating register information in a UVM-compliant model, engineers gain a powerful means to simulate, verify, and validate the behavior of the registers within the system.
UVM Register Layer:
The UVM Register Layer adds an additional layer of abstraction to the UVM Register Model. This layer enables a more modular and scalable approach to register modeling. With the UVM Register Layer, engineers can structure register models in a hierarchical fashion, mirroring the actual hierarchy of registers within the hardware design. This hierarchical representation enhances reusability and simplifies the verification process.
UVM Model Generation:
Generating a UVM Register Model involves a systematic process of defining registers, fields, and their relationships. UVM provides a standardized methodology for specifying register details and behaviors, ensuring consistency across the verification environment.
Automated tools for UVM Model Generation streamline the process, allowing engineers to efficiently create and update register models. These tools often integrate with register description languages, such as IP-XACT or SystemRDL, facilitating seamless communication between design and verification teams.
Integration for Comprehensive Verification:
Integrating the UVM Register Model into the overall verification environment is crucial for comprehensive testing. Through UVM's standardized methodology, engineers can create test scenarios that thoroughly exercise the functionality of registers under normal and exceptional conditions.
This integrated approach not only ensures that the functional aspects of the system are validated but also provides a platform for assessing security vulnerabilities related to register access and manipulation.
Conclusion:
In the intricate landscape of embedded systems, the amalgamation of functional safety and security is a requisite for success. The UVM Register Model, with its layered architecture and standardized methodologies, emerges as a key enabler for engineers striving to achieve both safety and security goals in their designs. By embracing these principles and leveraging UVM, developers can navigate the complexities of modern embedded systems with confidence, delivering products that meet the highest standards of reliability and resilience.